Fortifying Offshore Operations: Cybersecurity for Oil and Gas Platforms
INDUSTRY
Oil & Gas
CHALLENGES
Flow computers are critical components in the oil and gas mining platform offshore. Providing accurate measurement, calculation, and monitoring of fluid flow, they enable custody transfer, production optimization, regulatory compliance, and data-driven decision-making. In some cases, flow computers may even have the capability to perform control and automation.
In recent years, many governments have enforced strict requirements to collect data related to oil and gas, for various reasons including regulatory compliance, environmental monitoring, resource management, and economic planning. Our end user, an oil and gas giant, has to channel these offshore data through a wide distance via wireless communication to the monitoring center situated in the onshore IT infrastructure.
Wireless technology is convenient for remote monitoring and management, yet creates more threat vectors at the same time. Malicious actors can leverage this “convenience” to attack the oil and gas components. For example, they may steal a trusted machine’s credentials through social engineering or phishing emails, or exploit zero day vulnerabilities, to perform a pivot attack.
Typically, hackers target vulnerable devices that can cause huge damage—one of these is flow computers. A hacked flow computer in the oil and gas industry may produce inaccurate measurements, operational disruption, safety hazards, and regulatory violations, resulting in loss of trust, financial impact, and increased cybersecurity risks for the platform. Any of these are high stakes that our end-user wishes to avoid. Thus, BlackBear Cyber Security was tasked to safeguard the flow computer and essentially the full platform.
Offshore platforms have unique requirements in terms of communication security. Situated in remote and harsh environments, physical security measures are difficult to implement and maintain. Cloud based cyber security approach could be expensive to implement as the bandwidth are limited, considering it relies on communication channels such as satellite, radio, and microwave links. They have limited bandwidth for data transfer, restricting the deployment of security tools and the ability to send and receive real-time threat intelligence.
Thus, compared to normal industrial systems, not only is there higher risk of malicious acts or equipment breakdown, the damage and consequences are also higher in offshore oil and gas platforms. In order to collect data from offshore equipment, a proactive protection and alert system is absolutely necessary. We strived to implement a cybersecurity solution that is secure yet simple both from the implementation and maintenance standpoints.
SOLUTION PROVIDED
In our topology, oil and gas field devices are connected to the flow computer then to an edge computer, which processes the data before sending it to the monitoring center by MQTT protocol. The user can then monitor the data via SCADA UI. The topology is redundant to ensure high availability communication.
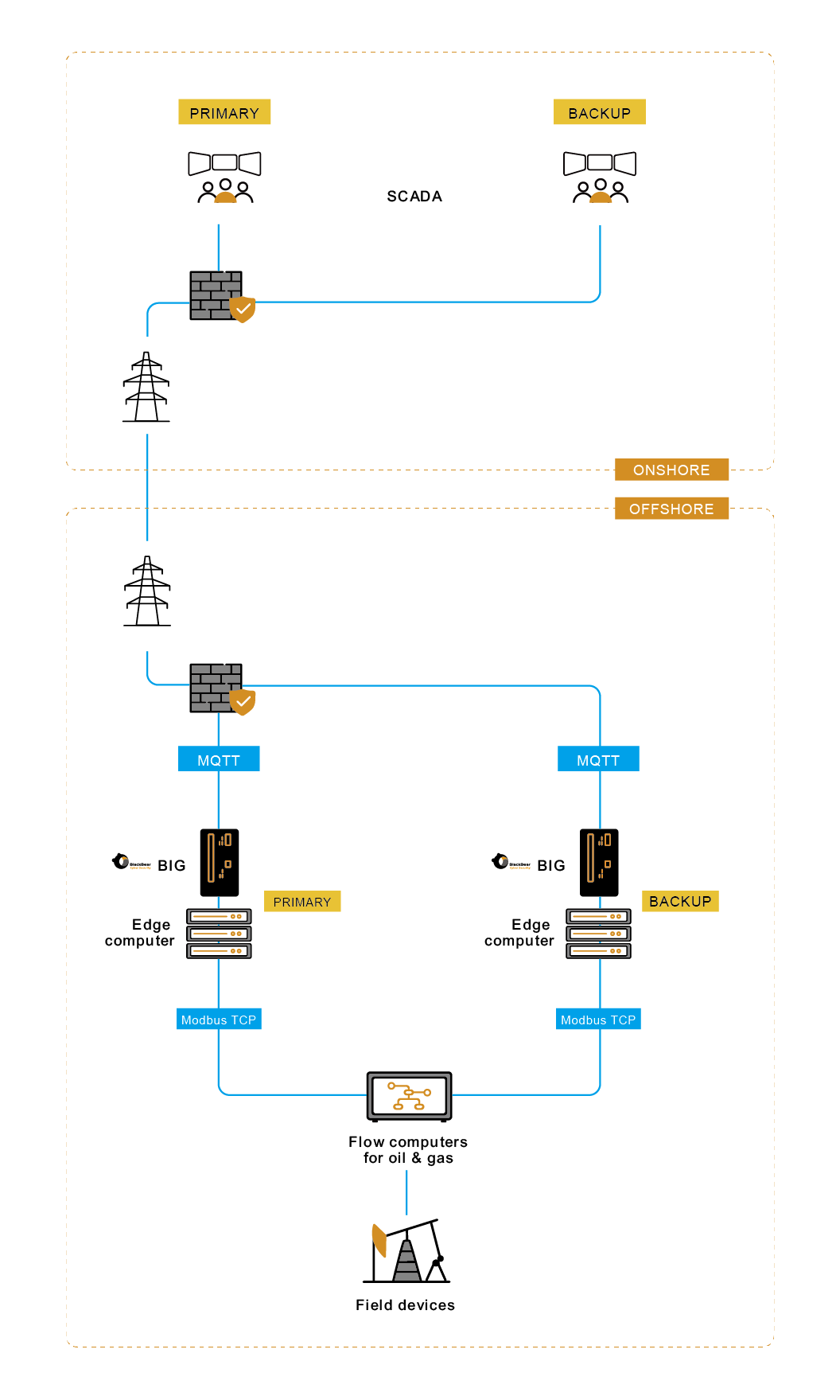
The BlackBear Intelligent Gateway (BIG) sits between the flow and edge computers, facilitating:
Cyber secured network
BIG incorporates a data diode that allows only one-way data traffic, and a network gateway that supports modbus TCP. Data can only flow from the flow computer to the uplink. No packets can travel into the flow computer, let alone malicious ones.
Therefore, it aids in secure data collection from the process side, while safeguarding these processes against malicious tampering or inadvertent errors from external sources.
High speed performance
The powerful computing power of BIG becomes apparent when we need to poll the data from hundred if not thousands of Modbus addresses.
Unlike normal software approaches that require more processing for data packets traversing across multiple network layers, BIG, as a physical layer security mechanism, is able to channel data at max. 1Gbps line rate.
Seamless operation
BIG has a unique feature where it is operating at a transparent mode, which barely affects system functionality, if at all. Even in well-established and running systems, the user does not need to modify SCADA settings to deploy BIG.
Ease of maintenance
The data diode offers security at the physical layer, which requires no configuration at all. This eradicates all human prone error and sets the mind at ease against misconfigurations.
For troubleshooting, BIG has a built-in packet sniffer, which users can enable or disable with ease through the UI. Usually when network issues arise, operators remote connect to the target device, but that is not the case when it comes to an offshore network, where data packets related to the mining operations need to be prioritized. Instead of remote connection, the operator can collect data packets and send the collected logs for analysis purposes.
Redundancy
Reliability is as important as security in critical infrastructure networks. To maintain the highest uptime possible, a redundant path was established to take over data transmission in case of physical damage or connection issues. A BIG is also included in this backup path, so cybersecurity is never compromised.
RESULTS
The BIG is very easy to configure, a very important feature for Operational Technology. Once the necessary requirements are determined with BlackBear experts, simply plug and play the received device to the existing network system. Offshore installation does have its difficulties due to limited personnel communication means, but BlackBear local representatives and technical team worked closely with the systems integrator, offering prompt support and facilitating the completion of a secure, reliable, remotely monitored platform.
Want to learn more about BlackBear Cyber Security solution applications? Reach out to our experts.


