Securing the Future: A Comprehensive Guide to OT Cybersecurity

- Securing the Future: A Comprehensive Guide to OT Cybersecurity
- 1. OT Systems and Cybersecurity
- 2. IT vs. OT Cybersecurity
- 3. OT Cybersecurity Solutions
- 4. OT Cybersecurity Best Practices
- 4.1 Network mapping and connectivity analysis
- 4.2 OT Asset Management
- 4.3 Privileged Access Management
- 4.4 Automatic Cyberattack Detection System
- 4.5 Applying Unidirectional Gateways
- 4.6 Increase cyber-aware capabilities and mindsets
- 5. Common Threats of OT Cybersecurity
- 5.1 Cloud Component Compromise
- 5.2 Legacy Systems and Old Vulnerabilities
- 5.3 Insecure Third-Party Connections
- 5.4 DDoS Attacks and IoT-botnets
- 5.5 Human Error and Misconfigured Software
- 6. OT Cyberattacks Classification
- 7. OT Cybersecurity Trends
- 7.1 Attacks Will Continue to Rise
- 7.2 Cyber-Informed Engineering
- 7.3 Increased Regulatory Compliance
- 7.4 Growing Investment in OT Security
- 8. How Do BlackBear OT Cybersecurity Solutions Work?
In the ever-evolving digital landscape, one aspect that has gained significant attention is OT cybersecurity. As our reliance on technology grows, so does the need for robust security measures, especially in the realm of operational technology (OT). But what exactly is OT cybersecurity, and why is it becoming increasingly important?
1. OT Systems and Cybersecurity

OT systems involve the hardware and software used to change, monitor or control physical devices, processes, and events in the enterprise. These can include everything from the systems that control a factory’s assembly line to the technology that manages a city’s traffic lights. OT systems encompass a wide range of technologies, from industrial control systems (ICS) to Supervisory Control and Data Acquisition (SCADA) systems. Each of these systems has specific cybersecurity needs and vulnerabilities that can be exploited by cybercriminals.
Historically, OT systems and IT systems operated independently. But with the advent of interconnected devices, the landscape has changed dramatically.
For example, recent statistics from the United States reveal that the average loss from an OT cyber attack escalated significantly. According to a report by IBM Security and the Ponemon Institute, the average cost of a data breach in the United States was $4.45 million in 2023. The same report found that the average cost of a data breach in the industrial sector (which includes OT systems) was $4.73 million, with the average cost per lost or stolen record being $165.
Moreover, in the past few years, the frequency of OT cyberattacks in the U.S. has shown a marked increase, highlighting the growing importance of robust cybersecurity measures.
This surge in cyber threats has led to OT cybersecurity becoming synonymous with industrial cybersecurity. A key strategy in this realm is ICS security, which encompasses both hardware and software cybersecurity measures. By integrating these measures, organizations can more effectively protect against the unique vulnerabilities present in OT systems. This comprehensive approach is essential for safeguarding critical infrastructure and maintaining operational continuity in the face of evolving cyber threats.
Operational Technology (OT) cybersecurity is the strategies and measures put in place to protect our critical operational systems from cyber threats. This involves safeguarding the systems that monitor and control physical devices, processes, and events in the enterprise. The key components of OT cybersecurity include network security, endpoint security, application security, and data security.
![]() See Also: What is Industrial Cybersecurity: Control System & Solutions
See Also: What is Industrial Cybersecurity: Control System & Solutions
1.1 ICS Security
Industrial Control Systems (ICS) are the crucial components under the broader umbrella of Operational Technology (OT). They play a key role in managing and monitoring industrial processes. These systems, which include Supervisory Control and Data Acquisition (SCADA) and Distributed Control Systems (DCS), are designed primarily for reliability and real-time performance, often placing cybersecurity as a secondary consideration. This inherent characteristic makes them particularly susceptible to cyber threats. It’s essential to note that an isolated OT is not necessarily a secure OT, emphasizing the need for a holistic security approach.
1.2 SCADA and DCS in OT Cybersecurity
SCADA, as a subset of ICS, is specifically used for monitoring and controlling geographically dispersed assets. These systems are central to the operations of utilities like gas and electric power transmission, where control functions are spread over large areas. On the other hand, DCS is another type of ICS employed mainly in continuous processing facilities, focusing more on localized control.
While ICS networks are mission-critical and demand high availability, their traditional design prioritizes operational efficiency over security. This has led to vulnerabilities that cybercriminals can exploit. Both SCADA and DCS, as practical applications of ICS, demonstrate this vulnerability in different operational contexts.
In the current industrial landscape, the distinction between SCADA and DCS within ICS highlights the diverse nature of cyber threats faced by these systems. Understanding these distinctions is key to developing effective cybersecurity strategies that address the unique challenges of each system.
![]() See Also: Enhancing Resilience: Solutions for Critical Infrastructure in Cybersecurity
See Also: Enhancing Resilience: Solutions for Critical Infrastructure in Cybersecurity
1.3 Benefits of High-quality Cybersecurity
High-quality cybersecurity in operational technology systems offers three key benefits: network and infrastructure optimization, minimized costs, and additional profitability. These advancements are crucial for addressing the growing demand for specialized security expertise, improving technological efficiency, and maintaining a competitive edge in the digital world.
- Network and Infrastructure Optimization
High-profile cybersecurity leads to the optimization of networks and infrastructure. This process involves a thorough evaluation of existing setups, identifying and addressing security gaps, and reconfiguring networks and equipment. This optimization is not just about enhancing security but also about improving the overall efficiency and effectiveness of the technological infrastructure.
- Minimizing Potential Costs and Financial Losses
Implementing high-profile cybersecurity measures can help minimize the potential costs associated with cyber-attacks, data breaches, and system downtime. Through robust cybersecurity, organizations can mitigate the risk of incurring such substantial financial losses.
- Adding Profitability
Furthermore, a strong cybersecurity posture enhances customer confidence and trust, which are invaluable assets in today’s digital marketplace. Consumers are increasingly aware of cyber risks and prefer doing business with companies that demonstrate a commitment to protecting their data. This preference can lead to increased customer loyalty, attracting new business and retaining existing clients, ultimately contributing to higher profits.
Therefore, beyond the direct financial savings from preventing cyber incidents, the broader implications of enhanced cybersecurity include maintaining a competitive advantage, fostering customer trust, and supporting business continuity. These factors cumulatively contribute to a company’s profitability, underscoring the importance of investing in high-profile cybersecurity measures as a strategic business decision.
2. IT vs. OT Cybersecurity

While IT and OT cybersecurity share the common goal of protecting systems and data from cyber threats, they are fundamentally different in their approach and focus. IT cybersecurity primarily focuses on protecting data from unauthorized access, alteration, or destruction. The core of IT security revolves around the CIA (Confidentiality, Integrity, Availability) model, ensuring that data remains confidential, maintains its integrity, and is readily available to authorized users.
On the other hand, OT cybersecurity is more concerned with the safety and reliability of systems that control physical operations. While data security is still important in OT, the primary focus is on preventing disruptions that could lead to physical harm or operational downtime. OT security adheres to the CAIC (Control, Availability, Integrity, Confidentiality) model. This model shifts the priority to maintaining control over physical assets to ensure safe operation at all times.
In summary, while both IT and OT cybersecurity aim to protect against cyber threats, their differing priorities reflect the distinct nature of the assets they safeguard. IT focuses on securing data, prioritizing confidentiality, whereas OT is more concerned with the continuous and safe operation of physical systems, placing a higher emphasis on control and availability.
| Aspect | IT Cybersecurity | OT Cybersecurity |
| Goal | Protecting data from cyber threats | Ensuring safety and reliability of physical operations |
| Environment | Data centers, cloud environments, office networks. | Industrial control systems, SCADA systems, manufacturing plants, critical infrastructure. |
| Primary Concern | Confidentiality, integrity, and availability of data | Preventing disruptions causing physical harm or downtime |
| Examples of Systems | Servers, databases, corporate networks | Industrial control systems, SCADA, manufacturing |
| Key Technologies Used | Encryption, IAM (Identity and Access Management), SIEM (Security Information and Event Management). | Industrial firewalls, IDS/IPS (Intrusion Detection Systems/Intrusion Prevention Systems), secure remote access. |
2.1 IT-OT Convergence
The convergence of IT and OT systems has brought significant benefits, such as enhanced data analytics and improved operational efficiency. By connecting OT systems to networks, enterprises can leverage the advantages of the ‘Extended Internet of Things’ (XIoT), which extends IoT concepts to industrial settings. This integration facilitates real-time monitoring, predictive maintenance, and smarter decision-making in industries.
However, with these benefits come increased risks. The interconnected nature of XIoT opens up OT systems to a broader range of cyber threats, previously limited to IT environments. This shift underscores the paramount importance of OT cybersecurity. Now, more than ever, securing OT systems isn’t just about protecting data; it’s about ensuring the safe and reliable operation of critical infrastructure, where a breach could have severe real-world consequences.
This convergence and the rise of XIoT highlight the need for a sophisticated approach to cybersecurity, blending IT’s data protection strategies with OT’s focus on physical process and safety. BlackBear intelligent gateways provide perfect cybersecurity for your crucial information.
3. OT Cybersecurity Solutions

When it comes to Operational Technology (OT) cybersecurity, several models and frameworks have been developed to guide and standardize security measures. These models provide structured approaches to addressing the unique challenges faced in securing OT environments. Let’s delve into three key frameworks that have become benchmarks in the industry: The Purdue Model, the MITRE ATT&CK framework, and the NIST Cybersecurity Framework.
3.1 The Purdue Model
The Purdue Model is a fundamental framework in OT cybersecurity, initially conceptualized to improve manufacturing processes. It presents a hierarchical architecture that categorizes network levels from physical equipment up to enterprise management systems. The model is structured into six levels, starting from Level 0 (physical process) and ascending to Level 5 (enterprise networks).
Key to this model is the segregation of OT and IT networks, minimizing the risk of cybersecurity threats traversing from IT systems to operational environments. Levels 0, 1, and 2 focus on direct interaction with physical processes, while Levels 3 to 5 shift towards IT-oriented tasks like site and enterprise operations. This demarcation is crucial in isolating sensitive OT networks from broader IT threats, ensuring that operational systems remain robust against cyber intrusions.
The Purdue Model’s layered approach simplifies understanding OT cybersecurity complexities and assists in designing secure industrial control systems. Its clarity and structure make it an essential tool in safeguarding OT environments from evolving cyber risks.
3.2 MITRE ATT&CK framework
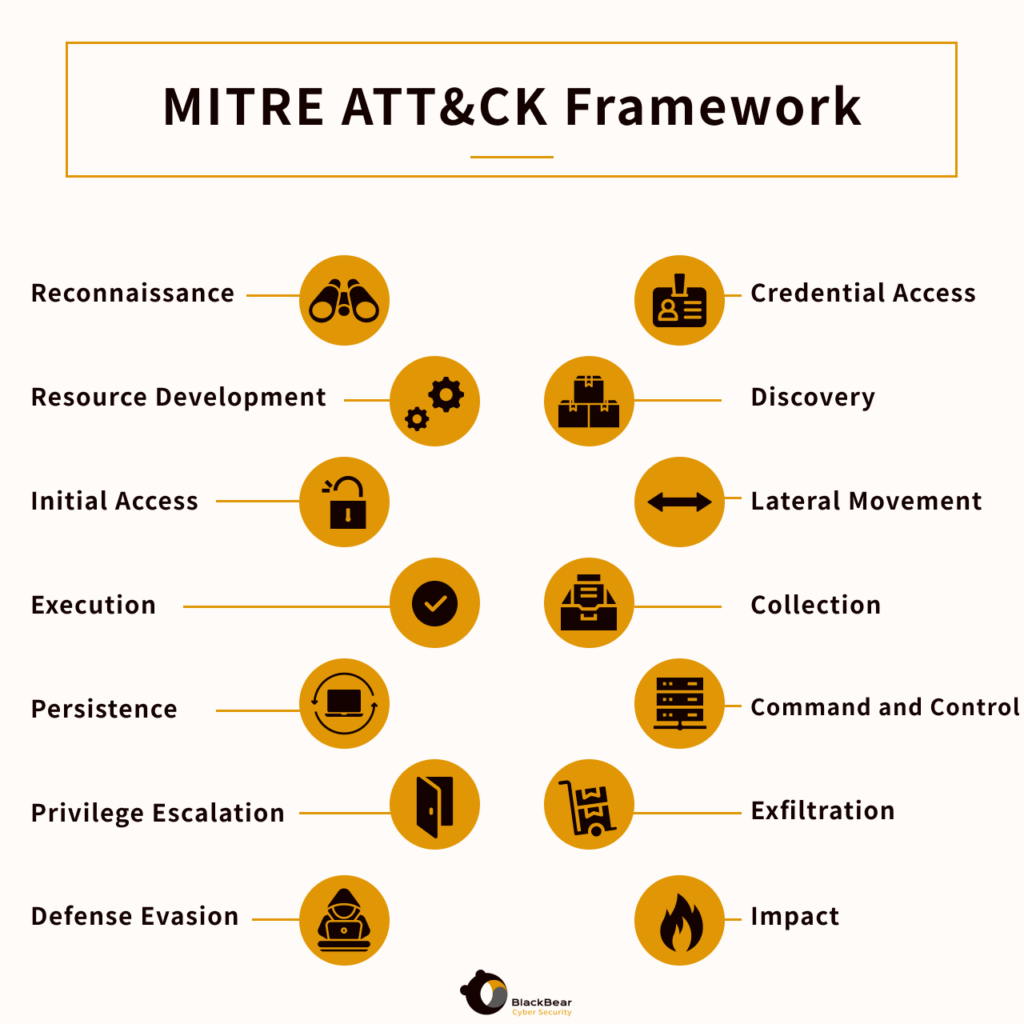
The MITRE ATT&CK framework is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations. This framework is used as a foundation for the development of specific threat models and methodologies in the cybersecurity community. It outlines a wide range of tactics and techniques that adversaries use to infiltrate and exploit networks and systems, providing a comprehensive language for discussing and sharing information about cyber adversary behavior.
MITRE ATT&CK guides the development of effective defense strategies by categorizing and detailing various attack methods, enabling security teams to anticipate, prepare for, and respond to different types of cyberattacks. It is particularly valuable because it is continuously updated with emerging threat patterns and tactics, ensuring that cybersecurity strategies remain relevant and effective against evolving threats. Its applicability to both IT and OT environments makes it an indispensable tool for organizations looking to strengthen their cybersecurity posture across all domains.
3.3 NIST Cybersecurity Framework
The NIST Cybersecurity Framework, developed by the National Institute of Standards and Technology, offers a comprehensive and flexible approach to managing cybersecurity risks. It is structured around five core functions: Identify, Protect, Detect, Respond, and Recover. This framework is widely recognized for its adaptability, allowing organizations to apply it according to their size, sector, or risk environment. It serves as an essential guide for developing robust cybersecurity strategies, especially beneficial in integrating IT and OT cybersecurity practices.
![]() See Also: Guide to Operational Technology (OT) Security: NIST Requests Comments | CSRC
See Also: Guide to Operational Technology (OT) Security: NIST Requests Comments | CSRC
![]() See Also: NIST Publishes Guide to Operational Technology (OT) Security
See Also: NIST Publishes Guide to Operational Technology (OT) Security
4. OT Cybersecurity Best Practices
Securing Operational Technology (OT) systems is more crucial than ever. This section outlines key best practices to fortify your OT infrastructure. From unraveling the complexities of network mapping and connectivity to mastering OT asset management, privileged access control, automatic cyberattack detection systems, and the smart use of unidirectional gateways. Each practice addresses a specific aspect of cybersecurity, creating a comprehensive shield against potential threats.

4.1 Network mapping and connectivity analysis
To establish a robust OT cybersecurity posture, it’s crucial to have a comprehensive understanding and control of your network’s connectivity. This begins with network mapping and connectivity analysis.
Network mapping is the process of visualizing and understanding all the connections and devices within your network. It allows you to identify how different components interact and communicate, providing valuable insights into potential vulnerabilities and attack pathways.
Connectivity analysis goes a step further. It involves examining the data flow within the network to understand how information is transmitted across different segments. This analysis helps in identifying unnecessary connections that may pose security risks, enabling you to streamline and secure the flow of data.
Together, network mapping and connectivity analysis form a proactive approach, allowing organizations to anticipate and mitigate risks before they escalate into security incidents. By gaining a deep understanding of your network architecture, you can enhance your control over network connections, leading to a more fortified and resilient OT environment.
4.2 OT Asset Management
Asset management involves identifying, classifying, and managing the physical and digital assets within an organization. In the realm of OT cybersecurity, effective asset management is a cornerstone. This systematic approach is more than an inventory exercise; it’s about gaining a clear picture of what assets exist, where they are located, and who has access to them.
Such detailed knowledge is vital in pinpointing potential security vulnerabilities. By understanding the specific attributes and locations of assets, organizations can tailor their cybersecurity strategies to protect critical elements more effectively. It also aids in risk mitigation, as knowing the intricacies of each asset allows for more targeted and efficient security measures.
Moreover, OT asset management is not static; it’s an ongoing process that evolves with the changing landscape of the organization’s assets. Regular updates and reviews ensure that the asset database accurately reflects the current state, which is essential in the dynamic environment of OT systems.
4.3 Privileged Access Management
Privileged Access Management (PAM), on the other hand, involves controlling who has access to critical systems and data. This ensures that only authorized individuals have the keys to your organization’s most sensitive and critical information. PAM acts as a gatekeeper, safeguarding against unauthorized access and potential breaches.
By narrowing down the circle of privileged users and meticulously monitoring their activities, PAM significantly mitigates the risks of insider threats. It’s not just about who has access, but also about how and when they access critical systems. This level of control and oversight is crucial in creating a secure OT environment, where each action by privileged users is accounted for and auditable. It’s a proactive measure in maintaining the integrity of your OT systems and the confidentiality of your data, playing a vital role in a comprehensive cybersecurity strategy.
The journey doesn’t end here. Once you’ve got a grip on your assets and their accesses, it’s essential to delve into configurations. For a deeper understanding of securing configurations, check out our take on secure configuration management.
4.4 Automatic Cyberattack Detection System
An Automatic Cyberattacks Detection System is an indispensable tool in the OT cybersecurity arsenal. This system operates by continuously monitoring network activity and automatically detecting anomalies that may indicate a cyberattack. Such systems are not just reactive; they are proactive in identifying potential threats before they can cause significant damage.
The effectiveness of these systems lies in their ability to provide comprehensive visibility into the OT environment. They can automatically discover and manage the full inventory of OT assets, offering real-time insights into the network’s operational status. This level of visibility is crucial for the early detection of unusual patterns or behaviors that could signify a cyber intrusion. In today’s fast-evolving cyber threat landscape, having such a system in place is vital for maintaining the integrity and resilience of OT networks.
4.5 Applying Unidirectional Gateways
As OT environments evolve, so do the tools to protect them. One such advanced tool is the unidirectional gateway. This tool not only enhances the defense mechanism by blocking inbound threats but also ensures smooth, uninterrupted operations.
However, while they offer a fortified layer of protection, integrating them into older OT infrastructures can be a challenge. It’s like fitting a modern lock onto an antique door – care, precision, and strategy are essential. And once integrated, they demand meticulous upkeep to maintain their integrity and efficiency.
Furthermore, maintaining these gateways without breaching their one-way nature requires innovative strategies. Routine maintenance, updates, or system checks should be carefully planned to ensure that the gateway’s unidirectional integrity remains uncompromised. In summary, while unidirectional gateways offer heightened security in OT environments, they also necessitate a thoughtful and strategic approach to integration and maintenance.
4.6 Increase cyber-aware capabilities and mindsets
Elevating cyber-aware capabilities and mindsets is a critical component of OT cybersecurity. This approach involves fostering a culture where every member of the organization is aware of cybersecurity risks and their role in mitigating them. It’s about moving beyond mere compliance to a mindset where cybersecurity is a daily operational priority.
Proper incentives and training are essential in developing this mindset. Employees should be encouraged and rewarded for proactive cybersecurity behaviors. Regular training sessions will keep them abreast of the latest threats and best practices. This cultural shift ensures that cybersecurity is not just the responsibility of the IT department, but a collective effort involving everyone in the organization.
Creating a cyber-aware culture is a strategic investment in the human element of cybersecurity, significantly enhancing the overall security posture of the OT environment.
5. Common Threats of OT Cybersecurity
In OT cybersecurity, awareness of common threats is crucial to prevent significant operational and financial losses. These threats range from technological vulnerabilities to human factors. Here’s an overview of some key challenges:
5.1 Cloud Component Compromise
The adoption of cloud-based OT solutions introduces new security challenges. While these solutions offer benefits like scalability and redundancy, they also present risks, particularly when local production systems are connected to outsourced cloud components. DDoS attacks on cloud services can disrupt this communication, leading to operational interruptions. Furthermore, insufficient separation between clients in a cloud environment can lead to collateral damage from attacks on other services. Ensuring robust security measures for cloud components connected to OT environments is essential to mitigate these risks.
5.2 Legacy Systems and Old Vulnerabilities
Legacy systems in OT environments, sometimes dating back 30 years or more, present significant cybersecurity challenges. These systems often operate with outdated security measures, making them vulnerable to modern cyber threats. For instance, attackers have been known to exploit vulnerabilities in older Windows servers, using specially crafted malware to execute malicious code. The inherent limitations of these legacy systems, such as the inability to support current security controls or lack of regular updates, amplify the risks. For example, sensors installed on valves and connected to a network without internal hardening procedures can be easily compromised. The challenge lies in updating these systems while ensuring continuity in operations, as many of these systems are critical and cannot afford significant downtime.
5.3 Insecure Third-Party Connections
Third-party remote connections, which are often used to control OT devices, can be a major security weakness. Attackers can exploit these less-secured connections to penetrate internal networks. For instance, cybercriminals have attacked a vendor-created network, using it as a springboard to infect other connected devices. This threat is intensified by the fact that many OT environments now integrate with various third-party interfaces and APIs, which, if not properly secured, can become gateways for attackers. Ensuring these connections and interfaces have robust security protocols is essential to protect the integrity of OT systems.
5.4 DDoS Attacks and IoT-botnets
The proliferation of IoT devices in OT networks has opened new avenues for cyber threats like DDoS attacks and IoT-botnets. IoT devices often lack built-in security measures, making them easy targets for being co-opted into botnets. The Mirai attack is a notable example of how IoT devices can be used for large-scale DDoS attacks. These attacks can severely disrupt operations by overloading components with excessive queries, rendering them unable to function properly. As IoT device usage continues to grow, the threat of botnet DDoS attacks increases, making DDoS protection a crucial priority for OT cybersecurity.
5.5 Human Error and Misconfigured Software
Human error is a significant factor in OT cybersecurity. Employees can unintentionally introduce vulnerabilities into systems, for example, by installing unauthorized software or incorrectly configuring hardware. These actions can lead to malware infections or operational disruptions. Additionally, IT teams face challenges managing and updating a growing number of next-generation firewalls, with incorrect configurations potentially causing functional issues. Mitigating these risks requires a combination of organizational regulations, continuous employee training in cybersecurity awareness, and strict policies for critical processes in the OT network.
Addressing these challenges requires a comprehensive and proactive approach to OT cybersecurity, blending technological solutions with strategic human resource management.
![]() See Also: An In-depth Look at Hardware-based Cybersecurity
See Also: An In-depth Look at Hardware-based Cybersecurity
6. OT Cyberattacks Classification
Recognizing the diverse aims and approaches used in OT cyberattacks is crucial for organizations to proactively strengthen their defenses and tailor cybersecurity strategies. While attacks on operational technology (OT) and industrial control systems (ICS) have significantly increased since the discovery of Stuxnet, the limited number of well-documented attacks and lack of analysis from a broader perspective pose a challenge for defenders.
To address this need, the FireEye Operational Technology Cyber Security Incident Ontology (OT-CSIO) was developed to provide a structured methodology for classifying attacks and aid communication with executives. This framework focuses on high-level analysis, evaluating four key categories:
- Target: Distinguishing between attacks directly targeting ICS and those where ICS systems are incidentally impacted.
- Sophistication: Rating the complexity of the attack as Low, Medium, or High.
- Impact: Assessing the consequences, ranging from data compromise or theft to the degradation or disruption of operations, and in severe cases, the destruction of systems.
- Impacted Equipment: Identifying the affected Purdue Layer(s) of equipment, which helps in understanding the scope and scale of an attack.
Unlike other frameworks like MITRE’s ATT&CK Matrix, OT-CSIO focuses on the overall attack lifecycle and ultimate impacts, not the specific tactics, techniques, and procedures (TTPs) used at each stage.
By understanding these classifications, organizations can gain valuable insights into the types of attacks they are most vulnerable to, allowing them to prioritize their security measures and allocate resources more effectively. This integrated approach fosters a deeper understanding of the potential threats, enabling proactive defense mechanisms to be implemented.
7. OT Cybersecurity Trends
Here are some key OT cybersecurity trends based on BlackBear recent analyses and reports:
7.1 Attacks Will Continue to Rise
The global annual cost of cybercrime is predicted to exceed $8 trillion in 2023, reflecting a dramatic rise in both attack rates and associated costs. This surge is driven by several factors:
- Economic challenges: Economic factors like inflation and supply chain disruptions can create vulnerabilities that attackers exploit.
- An expanding attack surface: The growing use of technology in various aspects of life creates more entry points for attackers.
- Hacktivist activities: Environmental activists are targeting specific industries like mining and oil, adding another layer of complexity.
The alarming rise in cyberattacks is evident from the 38% increase observed globally in 2022 compared to the previous year. This escalation is fueled by the evolving ransomware ecosystem and the targeting of collaboration tools used in remote work environments.
As a result of this increasingly complex and evolving threat landscape, organizations must prioritize strengthening their OT cybersecurity measures to effectively mitigate the growing risks.
In response to this growing threat, organizations are increasingly focusing on enhancing their OT cybersecurity posture to mitigate the risks posed by ransomware attacks.
7.2 Cyber-Informed Engineering
The rise of Cyber-Informed Engineering is another notable trend in 2022. This approach emphasizes the importance of considering cybersecurity risks in the design and implementation of OT systems, ensuring that these systems are resilient to cyberattacks. By incorporating cybersecurity principles from the beginning, organizations can better protect their OT environments from potential threats.
7.3 Increased Regulatory Compliance
Regulatory compliance has become a more significant aspect of OT cybersecurity, with organizations facing increased scrutiny from regulatory bodies like the NIST Cybersecurity Framework and NERC CIP Nations. This has led to a higher demand for advanced cybersecurity products and solutions that cater to the unique challenges of OT environments.
7.4 Growing Investment in OT Security
Investment in OT security is expected to grow at a compound annual growth rate (CAGR) of 21%. This increased investment indicates that organizations are recognizing the importance of securing their OT systems and are taking steps to improve their cybersecurity posture. However, there is still room for improvement, as many organizations have not yet achieved a significant level of maturity in their OT security programs.
![]() See Also: What are Data Diodes? How They Work in Cybersecurity
See Also: What are Data Diodes? How They Work in Cybersecurity
8. How Do BlackBear OT Cybersecurity Solutions Work?
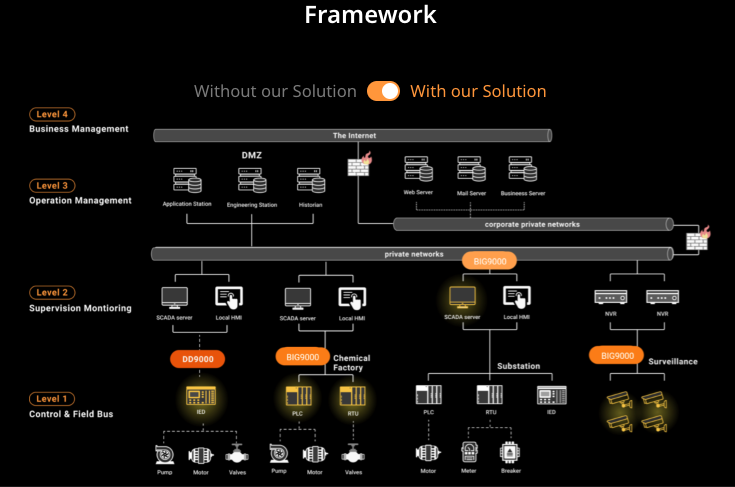
Our team of experts can help businesses identify potential vulnerabilities in their OT systems and respond effectively to cyber incidents.
In summary, BlackBear cybersecurity solutions for OT are a testament to our commitment to protect critical infrastructure. The architecture, as depicted in the network diagram above, integrates SCADA servers and secure communication channels between PLCs and RTUs.
Our devices, the BIG9000 and DD9000, serve as robust network interfaces, ensuring unidirectional communication and physical security at OSI layer 1. This advanced setup, complying with IEC 62443 standards and employing MACsec data encryption, provides a comprehensive shield against cyber threats.
To explore how our state-of-the-art OT cybersecurity solutions can bolster your operational technology, we invite you to visit our website and see the difference expertise can make.
Your Network Security is Our Duty!

