What is Industrial Cybersecurity? A BlackBear Complete Guide

- What is Industrial Cybersecurity? A BlackBear Complete Guide
- 1. Understanding Industrial Cybersecurity
- 2. Organizational Infrastructure
- 3. Industrial Control Systems Cybersecurity
- 4. Common Threats To Industrial Cybersecurity
- 4.1 Telecommuting Risks
- 4.2 IoT Security Risks
- 4.3 Old Equipment Risks
- 4.4 Phishing Attacks
- 4.5 Ransomware
- 4.6 Intellectual Property Theft
- 4.7 Supply Chain Attacks
- FAQs
In an era where cyber-attacks can lead to severe operational disruptions, massive financial losses, and even potential safety hazards, industrial cybersecurity is a frontline defense that organizations cannot afford to ignore.
As security technologist Bruce Schneier wisely said “You can’t secure what you don’t understand,” and “the worst enemy of security is complexity.” These words ring especially true in the realm of industrial cybersecurity, where the systems we’re trying to protect are often complex and not fully understood by those tasked with securing them.
This article is designed to be your tour guide, highlighting the importance of industrial cybersecurity, unveiling its various aspects, and illustrating how solutions by BlackBear Cyber Security can elevate your organization’s cybersecurity posture.
1. Understanding Industrial Cybersecurity
What is industrial cybersecurity? Simply put, it’s the shield that protects the computer systems and networks that are the lifeblood of vital industries like manufacturing, energy, and transportation. It’s about keeping these sectors safe from the dangerous cyber threats that could cripple their operations.
As per the guidelines of NIST SP. 800-82, if the integration of operation and internet systems is not handled properly, it could compromise Operational Technology (OT) systems and Industrial Control Systems (ICS) due to blocked or delayed information flow.
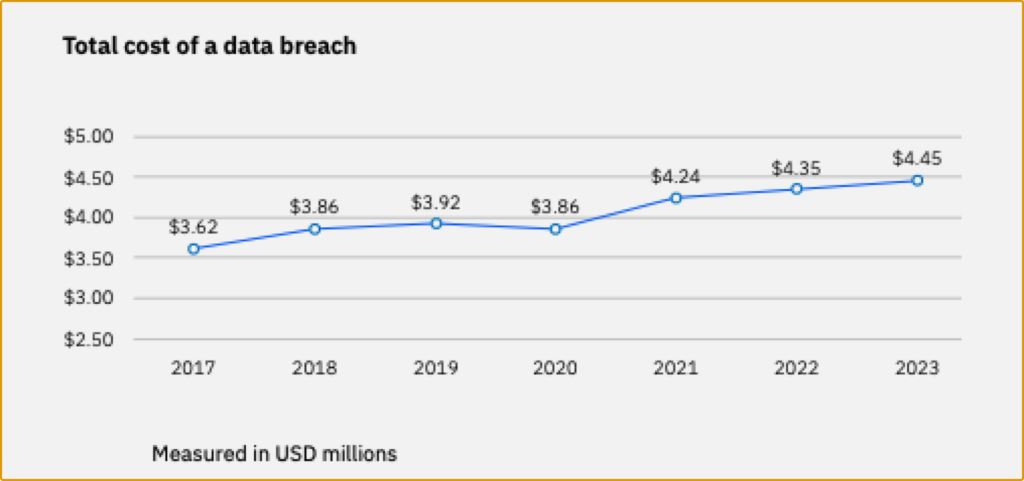
Moreover, according to a study, the worldwide average cost for a data breach in 2023 rose to USD 4.45 million, marking a 15% hike over 3 years. This underscores the critical importance of robust cybersecurity measures in the industrial sector.
 See Also: Industrial Control Systems | Cybersecurity and Infrastructure Security Agency CISA
See Also: Industrial Control Systems | Cybersecurity and Infrastructure Security Agency CISA
1.1 IEC 62443 Standard
The most comprehensive and exhaustive industrial cybersecurity standard is the IEC 62443 standard, a globally recognized framework for securing Industrial Control Systems (ICS) against cyber threats. Developed by the International Electrotechnical Commission, it offers clear guidelines to protect industrial systems and networks from digital vulnerabilities. This standard not only focuses on technical measures but also emphasizes organizational and operational strategies, providing a holistic approach to industrial cybersecurity. To explore the complete IEC 62443 series of standards, visit ISA’s dedicated page.
Implementing the IEC 62443 standard in industrial control systems involves a series of strategic steps. It starts with a detailed risk assessment to identify system vulnerabilities, followed by creating a customized security program suited to the specific industrial environment. Essential actions include formulating robust security policies, improving system security architecture, and ensuring ongoing monitoring and maintenance. This approach not only counters existing threats but also equips the system with the ability to handle future cybersecurity challenges, safeguarding the industrial systems from potential disruptions.
2. Organizational Infrastructure

Operational Technology (OT) is similar to Information Technology (IT) but focuses on the technology behind industrial control systems (ICS). Essentially, while IT manages a company’s data, OT oversees the physical aspects of its operations.
2.1 IT (Information Technology)
The IT function centers on managing and processing data, such as data storage, retrieval, and transmission. The primary goal is to ensure the confidentiality and integrity of data. It involves the use of devices like computers, servers, and networking devices, which are characterized by their strong data processing capabilities, high-speed networking, and robust cybersecurity measures.
 See Also: Unidirectional Gateway: Types, Benefits & Applications
See Also: Unidirectional Gateway: Types, Benefits & Applications
2.2 OT (Operational Technology)
This function is responsible for controlling and monitoring physical processes, concentrating on the direct management of physical equipment. Devices used in this context include Programmable Logic Controllers (PLCs) and SCADA systems, which are tailored for reliability and continuous operation, even in demanding environments.
2.3 ICS (Industrial Control Systems)
Industrial Control Systems are a subset of OT, and specifically refers to the control systems used in industrial settings to manage and automate processes. ICS plays a crucial role in managing and optimizing processes in sectors where physical control is paramount. Key devices in this area include Distributed Control Systems (DCS) and Supervisory Control And Data Acquisition (SCADA), which are optimized for overseeing industrial operations while ensuring continuous process flow and safety.
 See Also: Securing the Future: A Comprehensive Guide to OT Cybersecurity
See Also: Securing the Future: A Comprehensive Guide to OT Cybersecurity
3. Industrial Control Systems Cybersecurity

IT and OT may seem like two separate functions, but with the rise of Industrial automation and Internet of Things, the boundaries have become vague. ICS cybersecurity must stand between industrial control systems and cyber threats originating from both OT and IT, ensuring that IT’s digital commands and OT’s physical actions are securely executed. This integration is essential for managing the efficiency and safety of industrial processes, making ICS a unique and crucial element in cybersecurity.
ICS cybersecurity is crucial because of the increasing focus of cyber-attacks on physical processes, aiming either for ransom demands or causing harm to critical production systems. Attacks on these systems can have significant financial, operational, and safety consequences. The unique nature of ICS requires a distinct approach to security, as traditional IT security measures may not be suitable for the specialized devices and operational needs of ICS.
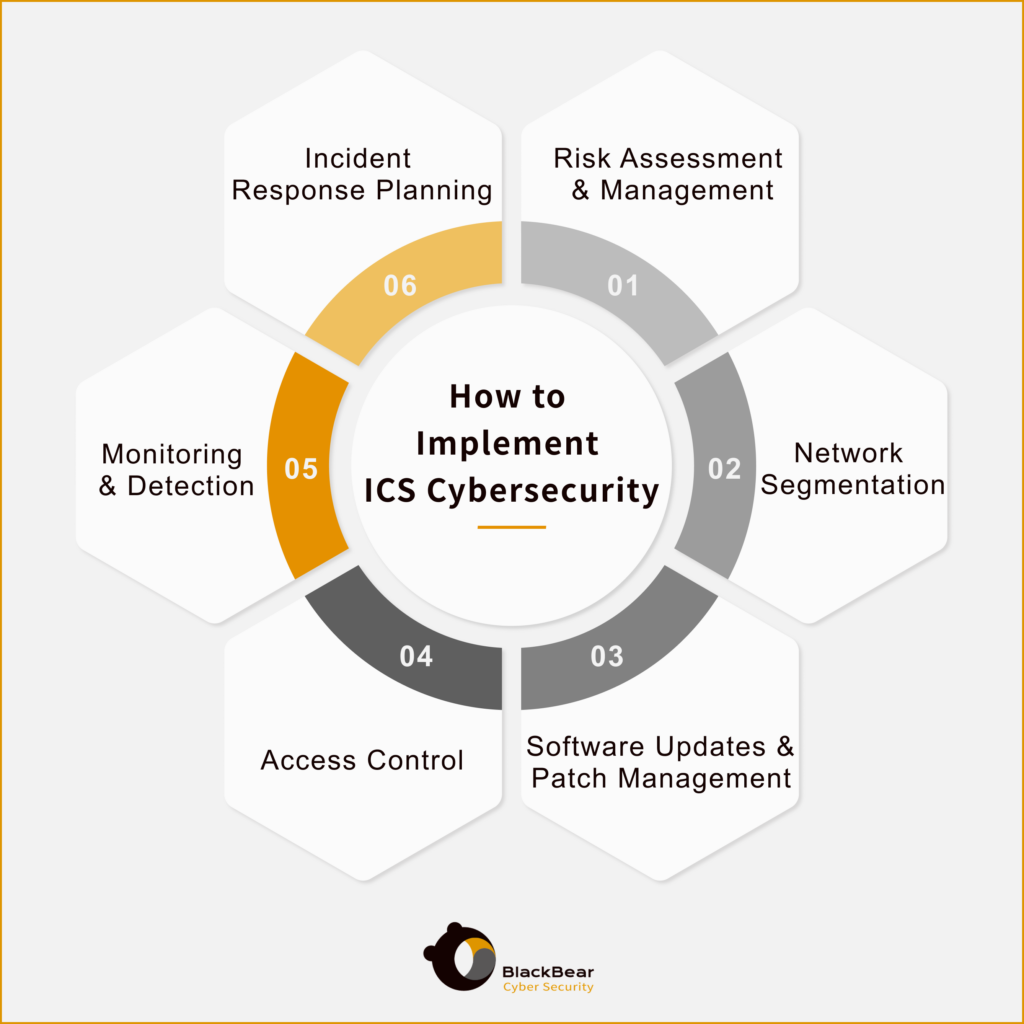
3.1 How to Implement ICS Cybersecurity?
Implementing ICS cybersecurity involves a series of best practices to protect industrial control systems from cyber threats. These practices typically include:
- Risk Assessment and Management: Conducting thorough risk assessments to identify and prioritize vulnerabilities.
- Network Segmentation: Separating ICS networks from business networks to minimize the risk of cross-contamination in case of a breach.
- Regular Software Updates and Patch Management: Keeping all software and systems up to date to protect against known vulnerabilities.
- Access Control: Implementing strict access controls and authentication procedures to ensure only authorized personnel can access critical systems.
- Continuous Monitoring and Detection: Establishing robust monitoring systems to detect and respond to suspicious activities in real-time.
- Incident Response Planning: Developing and regularly updating an incident response plan to quickly address and mitigate the impact of a cyber attack.
 See Also: Enhancing Resilience: Solutions for Critical Infrastructure in Cybersecurity
See Also: Enhancing Resilience: Solutions for Critical Infrastructure in Cybersecurity
4. Common Threats To Industrial Cybersecurity
In recent years, several high-profile cyberattacks demonstrated the variety and severity of threats facing industrial cybersecurity. Notable incidents include the Ukrainian State Nuclear Power Company Attack, and Greek Natural Gas Distributor Attack. The manufacturing industry is also a top target of ransomware attacks.
These high-profile attacks are just the tip of the iceberg, highlighting the need for comprehensive and dynamic security strategies. Specific threats that pose significant risks to industrial cybersecurity include the challenges of remote management, the vulnerabilities in IoT (Internet of Things) devices, the risks associated with old equipment, and the ever-present dangers of phishing attacks. Furthermore, the growing concerns over ransomware, the theft of intellectual property, and the vulnerabilities within the supply chain will also be discussed.
4.1 Telecommuting Risks
Remote management is a huge benefit of industrial digitalization, as many industrial sites are wide-spread, remote, or within harsh environments. Yet, remote access often lacks the robust security measures found in on-site settings. To mitigate these risks, companies should implement secure VPNs, enforce multi-level access segmentation, and provide regular cybersecurity training to employees.
4.2 IoT Security Risks
The integration of IoT devices in manufacturing increases efficiency but also introduces significant security risks. These devices, often connected to the internet, can be vulnerable to cyberattacks. To protect against IoT security risks, manufacturers should use secure, authenticated IoT devices, apply network segmentation to isolate them from critical networks, and continuously monitor IoT device activity for any unusual behavior.
4.3 Old Equipment Risks
Legacy equipment in manufacturing can be a major cybersecurity risk due to outdated security features. These older systems might not be compatible with modern security updates, leaving them vulnerable to attacks. To address this, manufacturers should regularly assess and update their equipment. Where updates aren’t possible, implementing additional security layers around the legacy systems or segmenting them from the rest of the network can help mitigate risks.
4.4 Phishing Attacks
Phishing attacks, involving malicious emails or websites, are common in the manufacturing industry. These attacks can lead to data breaches or malware infections. To combat phishing, it’s important to establish layers of cybersecurity defenses and foster a culture of awareness. Regular training for employees to recognize and report phishing attempts is essential.
4.5 Ransomware
Ransomware attacks encrypt data and demand payment for its release. They can disrupt manufacturing operations and lead to significant financial losses. To defend against ransomware, manufacturers should implement best cybersecurity practices, conduct regular security assessments, and maintain 24/7 network monitoring. Employee training on cybersecurity awareness is also vital.
4.6 Intellectual Property Theft
Intellectual Property (IP) theft can be devastating for manufacturers reliant on their proprietary information. Unauthorized access to manufacturing systems to steal data is a common method. Proactive measures like restricting access to sensitive information and monitoring for unauthorized activities are crucial for protecting IP.
4.7 Supply Chain Attacks
Supply chain attacks, where cybercriminals target a manufacturer’s network through its partners, can lead to data theft or operational disruption. Manufacturers should be cautious with the information shared with partners and implement regular security assessments. Using anti-virus software, implementing access controls, and ensuring physical security measures are also important steps.
 See Also: What are Data Diodes? How They Work in Cybersecurity
See Also: What are Data Diodes? How They Work in Cybersecurity
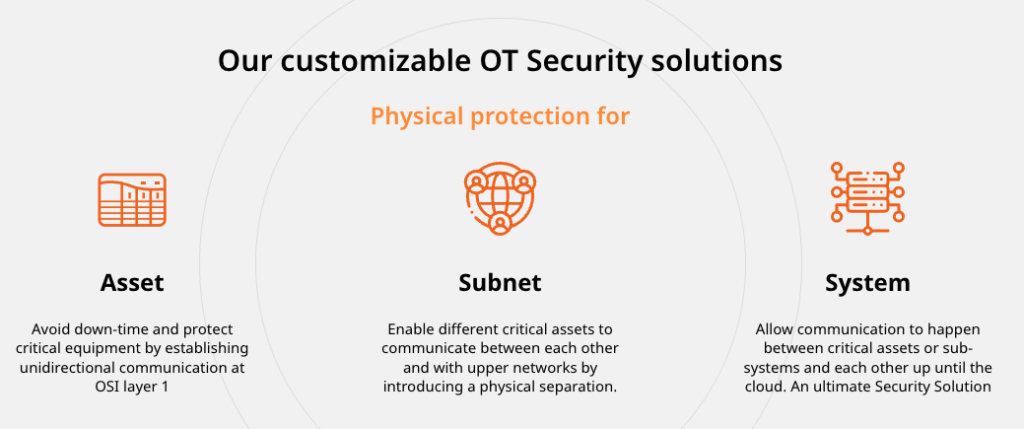
Contact BlackBear to Enhance Your Industrial Cybersecurity
In the rapidly evolving digital landscape, industrial cybersecurity is a significant concern for businesses worldwide. Knowing is only half the battle. Action is the key. So, take proactive steps towards enhancing your industrial cybersecurity with BlackBear Cyber Security. We’re equipped to address your industrial cybersecurity needs and help you fortify your business against the ever-evolving landscape of cyber threats.
FAQs
1. What Are the Major Vulnerabilities at Industrial Sites?
Major vulnerabilities at industrial sites include outdated PLC software, unpatched operating systems, unmonitored external access, and incorrect network segmentation. An often overlooked yet significant vulnerability is the human factor, where unaware employees may unknowingly compromise security. Continuous employee education as well as foolproof security measures are not just helpful but necessary.
2. Does Old Equipment Need to be Changed?
Old equipment does not always need to be replaced if it can be secured through threat detection and virtual patching. Effective asset management is key, ensuring that even older equipment complies with current security protocols. Asset Performance Management (APM) solutions are crucial in maintaining security across the equipment’s lifecycle.
 See Also: An In-depth Look at Hardware-based Cybersecurity
See Also: An In-depth Look at Hardware-based Cybersecurity
2. Will Cyber Attacks Become Frequent?
Yes, cyber attacks are becoming more frequent, targeted, and complex. The cybersecurity landscape is continually evolving, with a significant increase in attacks on industrial organizations. Continuous improvement in security solutions and employee training are essential to mitigate these risks.

